2-DES (Double)
Double-DES has two different encryption phases with two different keys (K_1, K_2) such that:
Ciphertext (Encryption): Enc (K2, Enc(K1, P))
Plaintext (Decryption): Dec(K1, Dec(K2, C))
Meet in the Middle Attack
Meet-in-the-middle is a known plaintext attack, that targets block cipher cryptographic functions, relies on exponentially reducing the number of brute force permutations required to decrypt text that has been encrypted by more than one key. The attacker applies brute force techniques to both the plaintext and ciphertext of a block cipher, where such an attack makes it much easier to gain access to data.
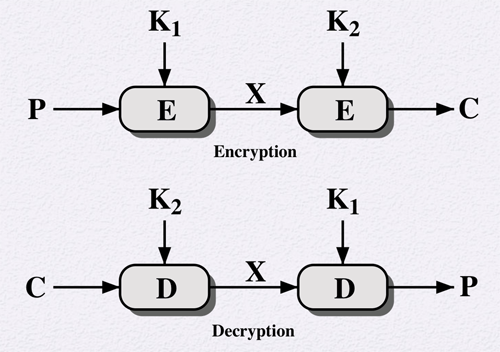
Let’s consider above encryption process:
Compute and Store P'(2^56) to X mapping encryptions by using different K_1’s. Then;
Compute and Store C'(2^56) to X mapping decryptions by using K_2’s.
Finally, compare X’s from two directions. If they yield the same, try with different known plaintexts (e.g. P”, C”). Hence, attacker effort would be O(2^56) instead of O(2^112) (c.f. single-DES efforts O(2^55)).
3-DES (Triple)
Triple-DES has two different encryption phases with three different keys (K_1, K_2, K_3) such that:
Ciphertext (Encryption): Enc(K3, Dec(K2, Enc(K1, P)))
Plaintext (Decryption): Dec(K1, Enc(K2, Dec(K3, C)))

3-Des Key Options
I. Option: K_1, K_2, K_3 are independent.
II. Option: K_1, K_2 are independent, K_2 = K_3.
III. Option: K_1 = K_2 = K_3 (equivalent to single-DES)
II. Option yields; Ciphertext (Encryption): Enc(K1, Dec(K2, Enc(K1, P))), where meet-in-the-middle attack efforts O(2^112)(c.f. double-DES efforts O(2^56)).
AES (Advanced Encryption Standard)
Due to limitations of DES (small key and block sizes), NIST started a open process to select a new block cipher and 15 proposals submitted to NIST around 1998. Rijndael (by V. Rijmen and J. Daemen) from Belgium chosen as the AES in 2001 after an open process, due to its security, performance, efficiency, implementability, and flexibility. Instead of Feistel Network, it’s a type of SPN (Substitution-Permutation Network) which will be written as another article soon.

AES has 128 bits (16 byte) block size with three allowable key sizes 128, 192, 256 (with # of rounds 10, 12, 14 respectively).
AES is iterated block cipher with rounds (different round keys) that processes the data as 4×4 matrix of 16 bytes total (each element is a byte) State Array.
Except for initial (AddRoundKey only) and final round (excluding MixColumns), all rounds go through the following steps:
SubBytes: substitution using look-up table, ShiftRows: row-based transposition,
MixColumns: column-based mapping, AddRoundKey: XOR with 16B round key (KeyExapnsion: round key generated), where each step is reversible.
O.S. Tapsin
Resources: https://internetofthingsagenda.techtarget.com/definition/meet-in-the-middle-attack — https://d3c33hcgiwev3.cloudfront.net/_dda2cef5cb570354314588046780ad4a_slides_3des_and_aes.pdf?Expires=1567641600&Signature=Z28SaH3H1Pk5dvDHg7gB~zh4f9W-rc3F8EvNSkoDoLt3Ou2LL3Cf8b7v0kph7YOVTU1-cF907ktqHuKonkNAhQurj-mBFptysyhvkdRSDpgRS5HAxjN22YQXRDpTBRBNPnzoBI0H9hlPgRrQwoaeEupLBVnKwjWYvMNAw2zvO6s_&Key-Pair-Id=APKAJLTNE6QMUY6HBC5A by Sang-Yoon Chang, Ph.D. — https://yhscs.y115.org/advanced/lessons/multipleEncryption.php — https://www.utdallas.edu/~muratk/courses/crypto09s_files/aes.pdf — https://pdfs.semanticscholar.org/df81/08646ba9242c9c337dabc293125ba8f5a8ff.pdf — https://www.researchgate.net/publication/221291825_High_Performance_Single-Chip_FPGA_Rijndael_Algorithm_Implementations —

This is a topic which is close to my heart… Many thanks! Where are your contact details though?
LikeLike
info@cryptoquantus.com -Thank you for your comment !
LikeLike
“Having read this I believed it was really informative. I appreciate you finding the time and effort to put this information together. I once again find myself personally spending a significant amount of time both reading and posting comments. But so what, it was still worthwhile!”
LikeLike
Thank you Akiko.
LikeLike
“This website really has all of the info I wanted about this subject and didn’t know who to ask.”
LikeLike
Thanks for great comment. You are alsways welcomed to ask your questions via info@cryptoquantus.com
LikeLike
Hey there! This is my first comment here so I just wanted
to give a quick shout out and say I genuinely enjoy reading through your articles.
Can you recommend any other blogs/websites/forums that cover the
same topics? Appreciate it!
LikeLike
Thanks for ones marvelous posting! I genuinely
enjoyed reading it, you are actually an excellent author.I will be sure to bookmark your
website and definately will return sooner or later.
I want to encourage that you just continue your great work, have got a nice
weekend!
LikeLike
Hello! I could possibly have sworn I’ve visited this website before but
after taking a look at a lot of the articles I realized it’s a new
comer to me. Regardless, I’m certainly happy I discovered it and I’ll be bookmarking it
and checking back regularly!
LikeLike
I actually have been exploring for a little
for just about any high quality articles or weblog posts within this kind of space .
Exploring in Yahoo I ultimately came across
this website. Reading this info So i’m satisfied to convey that We have an extremely good uncanny feeling
I discovered just things i needed. I this type of lot certainly can make sure to don’t overlook
this site and offer it a glance regularly.
LikeLike
Touche. Sound arguments. Keep up to date the great effort.
LikeLike
I love your writing style genuinely loving this internet site.
LikeLike
Muchas gracias. ?Como puedo iniciar sesion?
LikeLike
no tienes que iniciar sesión
LikeLike
Wonderful goods on your part, man. I’ve understand your stuff previous to and you are just extremely fantastic.
I actually like what you’ve acquired here, really like what you
are stating and how where you say it. You are making
it enjoyable and also you still care for to hold it sensible.
I can’t wait to read much more on your part. This can be actually a terrific website.
Have a look at my web blog; college ruled notebook 5 subject
LikeLike
Ahaa, its fastidious conversation about this post here at this blog, I have read all that, so at this
time me also commenting here.
LikeLike
My partner and I stumbled over here by a different website and thought I may as well check things out. I like what I see so i am just following you. Look forward to checking out your web page for a second time.
LikeLike
It’s nearly impossible to find experienced people for this subject, however, you seem like you know what you’re talking about! Thanks
LikeLike
Thank you for the good writeup. It in fact was a amusement account it.
Look advanced to more added agreeable from you! By the way, how could
we communicate?
LikeLike
Please don’t hesitate to contact via info@cryptoquantus.com
LikeLike