Before getting started with Block Cipher, digital computer communications based on bits, where 1 byte equals 8 bits. For instance, the word cryptoquantus consist of 13 characters (byte), so it equals to 8×13 = 104 bits .
ASCII (American Standard Code for Information Interchange) is an encoding representing each typed character by a number, where each number is stored in one byte {0..255}. Unicode is an alternative encoding for Mandarin, Greek, Arabic, etc. languages, typically 2-bytes per character. Hence, ASCII encoding represents, C-67, R-82, Y-89, P-80, T-84, O-79, Space-32 etc.
Block Cipher
Block Cipher function maps, n bits to n bits, where there are (2^n) possible block options. It’s also reversible function such as, Dec(key,(Enc(key, X)))=X, for all X (Plaintext). Ideal block cipher supports the maximum number of encryption mappings, where (2^n)! possible transformations or keys.
Feistel Cipher (Lucifer)

He was a German-born cryptographer who worked on the design of ciphers at IBM. He wanted an approximation of ideal block cipher, built out of components that are easily realizable and contributed to DES.
Feistel Cipher (Lucifer) is simply a Product Cipher that consist of a network for symmetric block ciphers.

F => stands for substitution
Right and Left intersection represents permutation (swap).
L_i: The left half of data after round i.
R_i: The right half of data after round i.
K_i: The sub-key for round i.
The i-th Round: L_i = R_i-1
R_i = L_(i-1) + F(R_(i-1), K_i)
There is no need for F to be reversible since decryption also uses F.
DES (Data Encryption Standard)
It’s the most widely used block cipher based on Feistel Cipher.
NBS (NIST) issued request for proposal for national cipher standard, In 1973 and adopted and published as DES, in 1977, developed by IBM (Feistel) and NSA.
Today, it’s considered as broken but there are still exist some applications.
DES Parameters
Block size: 64 bits, Key size: 56 bits, # of rounds: 16 rounds, Round function (F): maps 32bits to 32bits, Sub-key generation (K_i): maps 56 bits to 16*48 bits.
F (Round Function): (R_i) = 32 bits, (K_i) = 48 bits
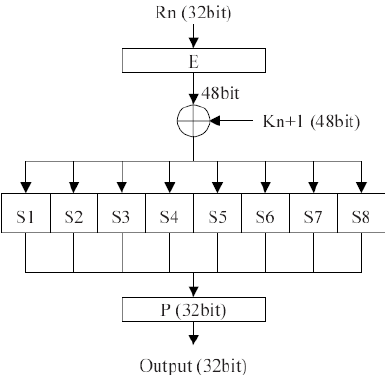
Sub-Key Generation (K_i)
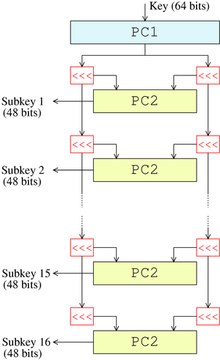
Here, PC’s stand for permuted choice, PC1(64 bits) to 56 bits, PC2(56 bits) to 48 bits.
DES Reliability
Due to Avalanche Effect, when an input is changed slightly, the output changes significantly e.g. flipping a single bit results half of the output bits flip.
DES & Brute Force Attack
For n-bits key, attacker efforts O[2^(n-1)] (where O notation describes the limiting behavior of a function when the argument tends towards a particular value or infinity) and requires to recognize the correct plaintext.
Trials on Brute Force Attacks:
In 1997: a few months In 1998: a few days
In 1999: 22 hours Today: ≈ 362 seconds
Hence, it’s said to be vulnerable against brute force attack.
O.S. Tapsin
Resources: https://d3c33hcgiwev3.cloudfront.net/_96a1f037a9f632673b9b6a8834a5262c_slides_block_cipher_and_des.pdf?Expires=1567468800&Signature=GT7YJzTahADJRbp8rLOPAhHDBa476tW0GbfTB5OpfN4Crxk4gI6T-AkH8trp~DD~-BcwPlGaQAwoMBiG8cQb9dEx–5-ZEeSJQtRBMsDU303nvdmDaOnffnqlKVMQL32oQ01k4b8upIPWXbUHJtHvommX9mTTzTcJOQlOsTGXX8_&Key-Pair-Id=APKAJLTNE6QMUY6HBC5A by Sang-Yoon Chang, Ph.D. — https://web.stanford.edu/class/cs101/bits-bytes.html — https://rob-bell.net/2009/06/a-beginners-guide-to-big-o-notation/ — https://arxiv.org/pdf/1003.4085.pdf — https://crypto.stackexchange.com/questions/752/how-long-does-it-take-to-crack-des-and-aes —

Hello there, I found your web site via Google while searching for a related topic, your web site came up, it looks good. I’ve bookmarked it in my google bookmarks.
LikeLike
I like what you guys are up too. Such clever work and reporting! Keep up the superb works guys I have incorporated you guys to my blogroll. I think it will improve the value of my website 🙂
LikeLike
I’m amazed, I must say. Seldom do I come across a blog that’s both educative and entertaining, and let me tell you, you have hit the nail on the head. The problem is something that not enough people are speaking intelligently about. Now i’m very happy that I stumbled across this in my hunt for something regarding this.
LikeLike
Greetings from Carolina! I’m bored to tears at work so I decided to browse your site on my iphone during lunch break. I enjoy the info you provide here and can’t wait to take a look when I get home. I’m surprised at how quick your blog loaded on my phone .. I’m not even using WIFI, just 3G .. Anyhow, good site!
LikeLike
Aw, this was a very nice post. In concept I would like to put in writing like this moreover – taking time and actual effort to make an excellent article… but what can I say… I procrastinate alot and on no account seem to get something done.
LikeLike
Excellent web site. Lots of useful info here. I am sending it to some friends ans additionally sharing in delicious. And obviously, thank you in your effort!
LikeLike
I do accept as true with all of the ideas you’ve offered on your post. They are really convincing and can definitely work. Nonetheless, the posts are very short for beginners. Could you please prolong them a bit from next time? Thanks for the post.
LikeLike
Actually I preferred to keep the posts short to open them discussion and comments. If you are interested, don’t hesitate to contact me on info domain.
LikeLike
Keep working ,splendid job!
LikeLike
Hey There. I found your blog using msn. This is a very well written article. I’ll be sure to bookmark it and come back to read more of your useful info. Thanks for the post. I will definitely comeback.
LikeLike
A formidable share, I just given this onto a colleague who was doing just a little analysis on this. And he in fact purchased me breakfast as a result of I found it for him.. smile. So let me reword that: Thnx for the deal with! However yeah Thnkx for spending the time to discuss this, I feel strongly about it and love studying more on this topic. If potential, as you change into experience, would you thoughts updating your blog with extra particulars? It is highly useful for me. Huge thumb up for this weblog post!
LikeLike
Hi there, just became aware of your blog through Google, and found that it is really informative. I am gonna watch out for brussels. I will appreciate if you continue this in future. Lots of people will be benefited from your writing. Cheers!
LikeLike
I just like the valuable info you supply on your articles. I’ll bookmark your blog and take a look at again right here regularly. I’m somewhat sure I will be informed plenty of new stuff right right here! Best of luck for the following!
LikeLike